1080p HD video recording with night vision, 135-degree wide-angle lens with motion filter, those are the hardware features at a glance provided by the “Circle” surveillance camera from Logitech. The online surveillance device, which runs at just under EUR 200, examined in a quick test at our IoT laboratory, delivered impressive results, thanks to its high level of protection.
Encrypted connections as a test criterion
When examining the online communication of the Circle, no unencrypted connections were detected in the quick test. As the monitoring and examination of the network traffic with the help of the Wireshark (https://www.wireshark.org/) analysis tool indicated, the complete communication occurred consistently secured by TLS 1.2 and offered solid protection against potential interlopers, such as man-in-the-middle attacks. In order to test the scenario, we implemented a test configuration with the tool mitmproxy , thereby trying to tap into the encrypted communication of the Logitech Circle. Yet even in this case, the Logitech server detected unauthorized certificates and prevented the transmission of video data. Unnoticed intrusion and tapping of video data or manipulation of such data is thus virtually impossible for potential third parties. The following illustration shows the result of our unsuccessful attack in Wireshark – the certificate we used is not known to the Logitech server and is therefore rejected.

Another positive aspect we noticed in terms of online communication was the fact that in the test, by means of monitoring with Wireshark, we were unable to determine any connections to third-party domains. This is in contrast to many other products, where there is frequently a wide array of data transmissions to domains that apparently do not belong directly to the manufacturer.
App security as a test criterion
For the corresponding Android app (tested version 1.5.495), Logitech did not reveal any serious vulnerabilities either. Thus, the criticism from the IoT lab at AV-TEST is in fact more of a theoretical nature, yet it still offers potential for optimization: As it was, the degree of code obfuscation was indeed high, yet overall, code obfuscation is not implemented consistently enough. As the following illustration with the excerpt of the class diagram of the application indicates, a large part of the relevant functions is concealed (recognizable by the class name one letter long), yet by contrast, a significant portion is not.
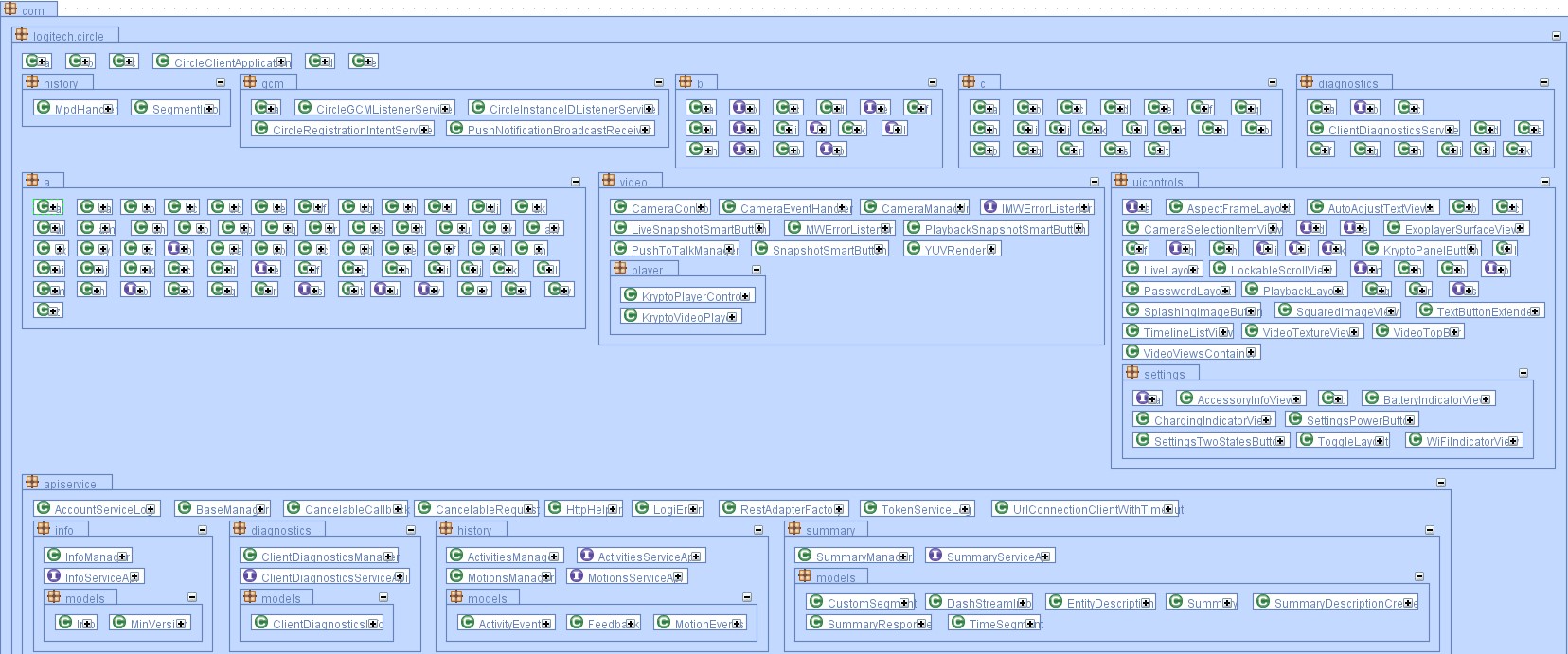
Theoretically, an attacker could exploit this situation in order to use tools such as Apktool (https://ibotpeaches.github.io/Apktool/), with which each random Android application can be decoded with relative certainty, and any of a vast number of JAVA decompilers in order to perform a reverse engineering, thus receiving access to security-relevant code and the app’s mode of operation. Potential reverse engineering is also additionally abetted here due to the fact that the outputs of the app on the logcat Android system console are relatively exhaustive, even if they do not contain directly apparent critical information. The following illustration shows an excerpt of the logging for the application. Function calls and the resulting program routine can be viewed there – potentially interesting information for reverse engineering.

For users with a rooted smartphone, it is also important to know that the user credentials are stored in plain text in the app folder. Without root rights, no other app can view them there, which is why we do not rate this factor as a vulnerability. With root rights, the username and password is open for any app explicitly on the lookout for this information, however. The following illustration contains an excerpt from the user information saved locally on the smartphone.

Conclusion
Overall, in the quick test, the Logitech Circle proved to be a solid product, revealing no vulnerabilities and earning the full 3-star rating in the quick test category.

