Updated findings (23. February 2017): Smartfrog reacted promptly and worked on a new App version and firmware update that fix the critical problems outlined below. With the new versions, Smartfrog now passes the security testing with 3 out of 3 stars.
With 1,280 x 720 pixels and 30 frames per second, the Smartfrog Cam offers decent picture quality, which is made complete by sound recordings using the integrated microphone. Even more exciting, however, are certain additional functions on the device, e.g. the geofencing feature. This enables the Smartfrog to be configured so that the camera begins security monitoring when the user leaves the designated home zone and ends as soon as the linked smartphone is within range again. Another fascinating feature are the daily summaries in time lapse. With this function, events recorded throughout the day can be played back in just a few minutes. Yet despite these smart features, the Smartfrog is anything but first choice, as the camera proved less smart in the security check performed in our IoT labs. The cam exhibited some major gaffes that led to downgrading in several categories, thus preventing a good rating.
Online transmission poorly or not encrypted (Update: Fixed!)
Updated findings (23. February 2017): All of the critical security problems have been fixed with the latest App release and the update for the camera. The findings of the initial test are still listed below for reference for our readers. A detailed review of the current versions will be published on this blog.
The Smartfrog exhibited initial severe problems during the online transmission of the video material: Although the majority of the established connections were secured via the TLS protocol in version 1.2, more careful analysis with the tools Wireshark and mitmproxy also revealed connections that were secured either insufficiently or not at all. As a result, during registration of the device, for example, it was possible to read unprotected critical information, including the UUID, as well as the assigned device name.
But it gets worse: The login via the Android application (tested version 2.2.0) was also insufficiently secured, allowing the interception of the account name and password during registration, as well as during a password change. Here as well, we used the tool mitmproxy to intercept the data from an existing connection. The following illustrations show how the account details were intercepted with mitmproxy during registration and when changing the password.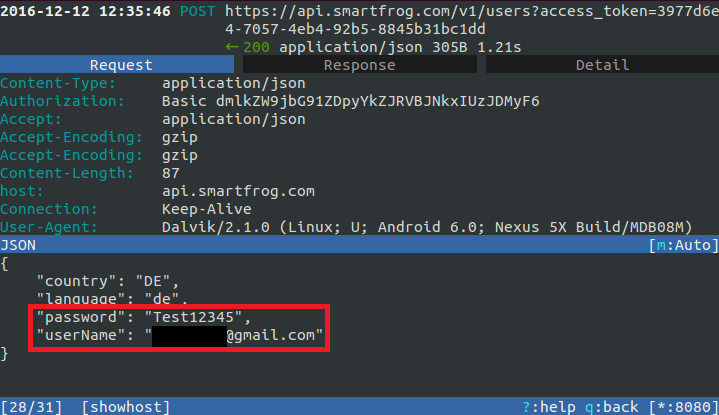

The problem in this case was not insufficient protection of the connection, but rather the inadequate implementation of security functions. For example, the system failed to check the certificates used for encryption. This enables attackers to divert the entire communication by means of a man-in-the-middle attack, and through the use of own certificates, to decrypt, read out and forward it re-encrypted.
In addition to these two problems, we also discovered that the live preview image of the camera stream displayed in the app was transmitted unsecured via HTTP and thus in principle could possibly be viewed by anyone. Naturally, this can also reveal potentially sensitive information.
The Android application also failed to provide protection through code obfuscation, which means that attackers can gain access to non-obfuscated source code and ultimately to potentially security-critical functions. In addition, an unencrypted log file, stored unprotected on the SD card, provides further critical information for possible reverse engineering. The log file contains information on the server domains, IPs, ports and secure tokens used. The following illustration shows an excerpt from this log file. In this manner, attackers could obtain a fairly detailed view of the application’s mode of operation, along with the corresponding security mechanisms.
Conclusion
Updated findings (23. February 2017): As pointed out above, the critical security problems have been fixed by Smartfrog. With the updated firmware of the camera and the smartphone App the security rating improved from 1 to 3 out of 3 stars. A detailed review of the current versions will be published on this blog.
Overall, the vulnerabilities revealed warrant a considerable downgrading of the Smartfrog. In our assessment, security is seriously jeopardized in several places due to implementation and design flaws, therefore, overall, the product can only be rated with 1 out of 3 stars in our quick test category.

